Problem Overview
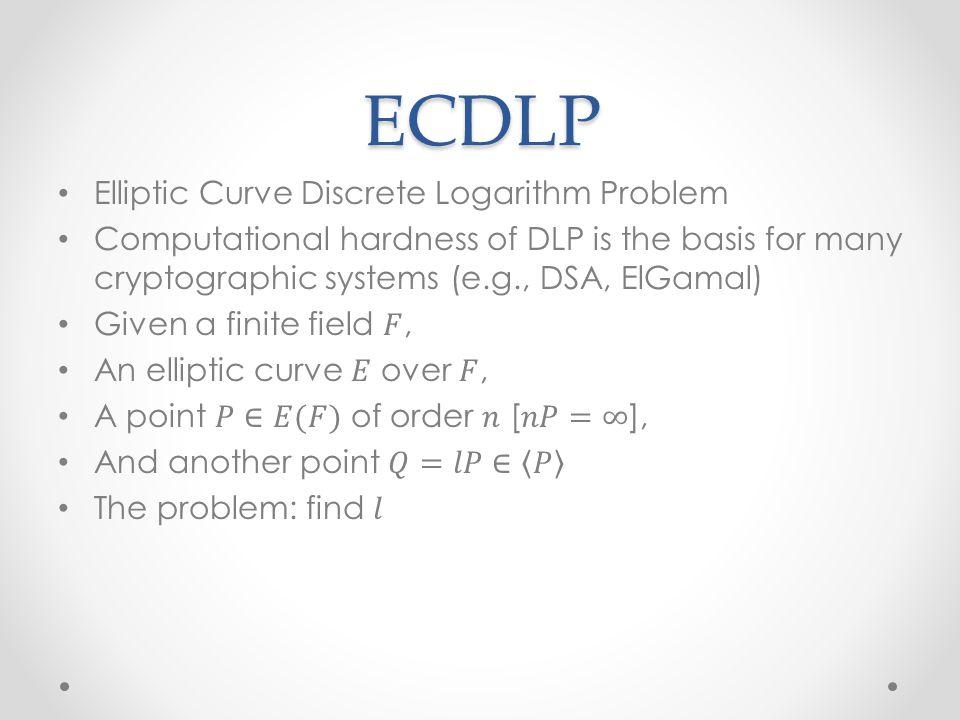
ECDLP, the discrete logarithmic problem on the elliptic curve. In 1987, Koblitz constructed ECDLP using the Abelian addition group formed on an elliptic curve. Experiments have proven that the key to 160bits can be comparable to the security of the RSA algorithm of the 1024BITS key in the elliptic curve encryption algorithm, and the gap between the security between the analog numbers is violently increased. Therefore, it can provide a faster, a public key cryptographic system with a smaller key length, and has a wide concern of people, providing people with powerful, such as implementing data encryption, key exchange, digital signature. tool.
ECC
In 1976, Diffie and Hellman published a "Cryptographic New Trend" due to symmetry encryption algorithms. The article introduces the concept of public key encryption, and raised RSA algorithms by Rivet, Shamir, and Adelman.
With the improvement and improvement of the decomposition, the improvement of computer speed and the development of computer networks, in order to ensure data security, the Key of RSA needs continuously, but the increase in key length causes The speed of its decryption is greatly reduced, and hardware implementation has become more and more unbearable, which has a heavy burden on the use of RSA, so there is a new algorithm to replace RSA.
1985 N.Koblitz and Miller proposes to use an elliptic curve for a cryptographic algorithm, depending on the discrete logarithmic problem ECDLP in the dot group on the oval curve on a limited domain. ECDLP is a more difficult problem than factor breakdown, which is the difficulty of the index level.
principle
The discrete logarithmic problem on the elliptic curve ECDLP is defined as follows: give a given number P and elliptical curve E, Q = KP, in the case of known P, Q A positive integer k is less than P. It can be proved to be comparable to the calculation of K and P, and the K and P calculate K is more difficult.
Corresponding to the additional calculation in the elliptic curve corresponds to the model of the multiplication of the discrete log, the multiplication operation in the elliptic curve corresponds to the diameters in the discrete logarithm, we can establish The corresponding cryptographic system of the elliptic curve.
For example, corresponding to the Diffie-Hellman public key system, we can implement on the elliptic curve by selecting the generation element P on E, which is required to be more enough, communication between the groups. And B separately select A and B, A, and B, but the AP and BP are disclosed, the Keys between the A and BCCCs are ABP, which is unable to know.
The corresponding ELGAMAL password system can be implemented on the elliptic curve as follows:
Embed the plain text M into the E-PM point, choose a little B∈E, each user Select an integer a, 0
k = kg [where K, G is the point on EP (A, B), K is an integer of less than N (n is the order of point G)]
It is difficult to find that K and G are given according to the addition of the addition, the calculation K is easy; but given K and G, seeking K is relatively difficult.
This is a challenge adopted by an elliptic curve encryption algorithm. We refer to the base point, k (public key).
related comparison
ECC with RSA Compare
ECC and RSA, there are absolute advantages in many ways, mainly reflected in the following:
anti-aggressive. The same key Length, its anti-aggressivity is strong.
The amount of calculation is small, the processing speed is fast. The total speed of ECC is much faster than RSA, the DSA is much faster.
The storage space takes up. The key size and system parameters of ECC are much smaller than RSA, and DSA means that it is much smaller. This is very important for encryption algorithms on the IC card. < / p>
Bandwidth requirements. When the long message is decrypted, the three types of cryptographic systems have the same bandwidth requirements, but the ECC bandwidth requirements are much lower when applied to short messages. Bandwidth requirements are low to make ECC in wireless The network field has a wide range of application prospects. These features of
ECC will replace RSA, become a common public key encryption algorithm. For example, the set of SET protocol has put it as the next generation set protocol. The provincial public key cryptographic algorithm.
The following is a comparison of the security and speed of RSA and ECC.
| Breaking time (MIPS year) | RSA / DSA (Key length) | ECC key length | RSA / ECC key length ratio | ||||||||||||
| 10 | 512 | 5: 1 | 10 < / p> | 768 | 6: 1 | 10 | 1024 | 160 | 7: 1 | 2048 | 210 | 10: 1 | 10 | 21000 " 140>600 | 35: 1 |
RSA and ECC security die length comparison
| function | security builder 1.2 | BSAFE 3.0 | |||
| 163-bit ECC (MS) | 1,023-bit RSA (MS) | 3.8 | 4, 708.3 | ||
| Signature | 2.1 (ECNRA) | 228.4 < / p> | |||
| 3.0 (ECDSA) | < Td width = "210"> | ||||
| authentication | 9.9 (ECNRA) | 12.7 | 10.7 (ECDSA) | < / TR> | |
| Diffie-Hellman key exchange | 7.3 | 1,654.0 |
RSA and ECC speed comparison